Concepts
CipherStash Identify
CipherStash End to End Identity works with the CipherStash Proxy to enable individual customer identity and context information to be associated data access event logs for auditing.
What problem is End-to-End Identity solving?
Complete visibility of data access requires the capability to identify the user making the access request.
Database access is often tied to deployed application or service rather than an actual user identity. Applications connect to the database on behalf of users, creating an identity mismatch. PostgreSQL does have role-based authentication, but in most cases it is used to narrow the permissions for the database connection initatied by an application. Associating database access controls with an individual identity requires additional effort and is not covered by database statement logging.
End to End Identity provides:
- passthrough identity to associate a JWT with data access events
- passthrough context information for refining search and audit analysis
- configurable identity provider for JWT verification
How End-to-End Identity Works
Trusted Issuer and Audience
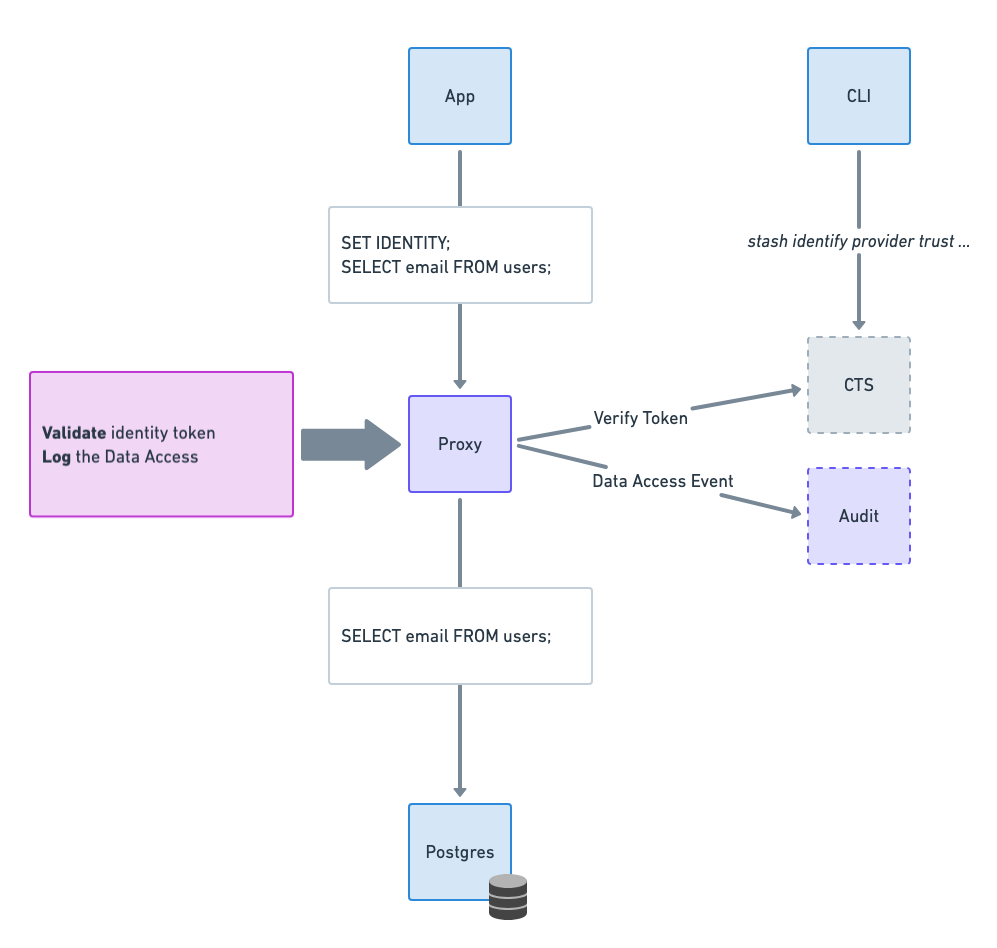
Using the CipherStash CLI, trusted Issuers and Audience can be added to a workspace. The provider details are used by the Proxy to verify client tokens.
See Configuring an Identity Provider.
Passthrough Identity
Passthrough Identity enables you to connect every SQL statement with real-world identity.
Using a custom SET CS_IDENTITY sql command, an end-user JWT is passed to the Proxy and validated.
The Proxy uses the CipherStash Token Service to verify the JWT, extracts subject (sub) and audience (aud) data from the token, and associates this client identity information with data access events.
See the Set Identity Command.
Passthrough Context
Passthrough Context provides the flexibility to associate a SQL statement with any additional contextual information you may need.
With Passthrough Context, collection of key/values can be passed to the Proxy using using a custom SET CS_IDENTITY sql command. The context information is associated with any data access events for refining search and audit analysis.
See the Set Context Command.
Architecture Diagram