Encryption in use: 3 ways to protect sensitive data in Typescript backends
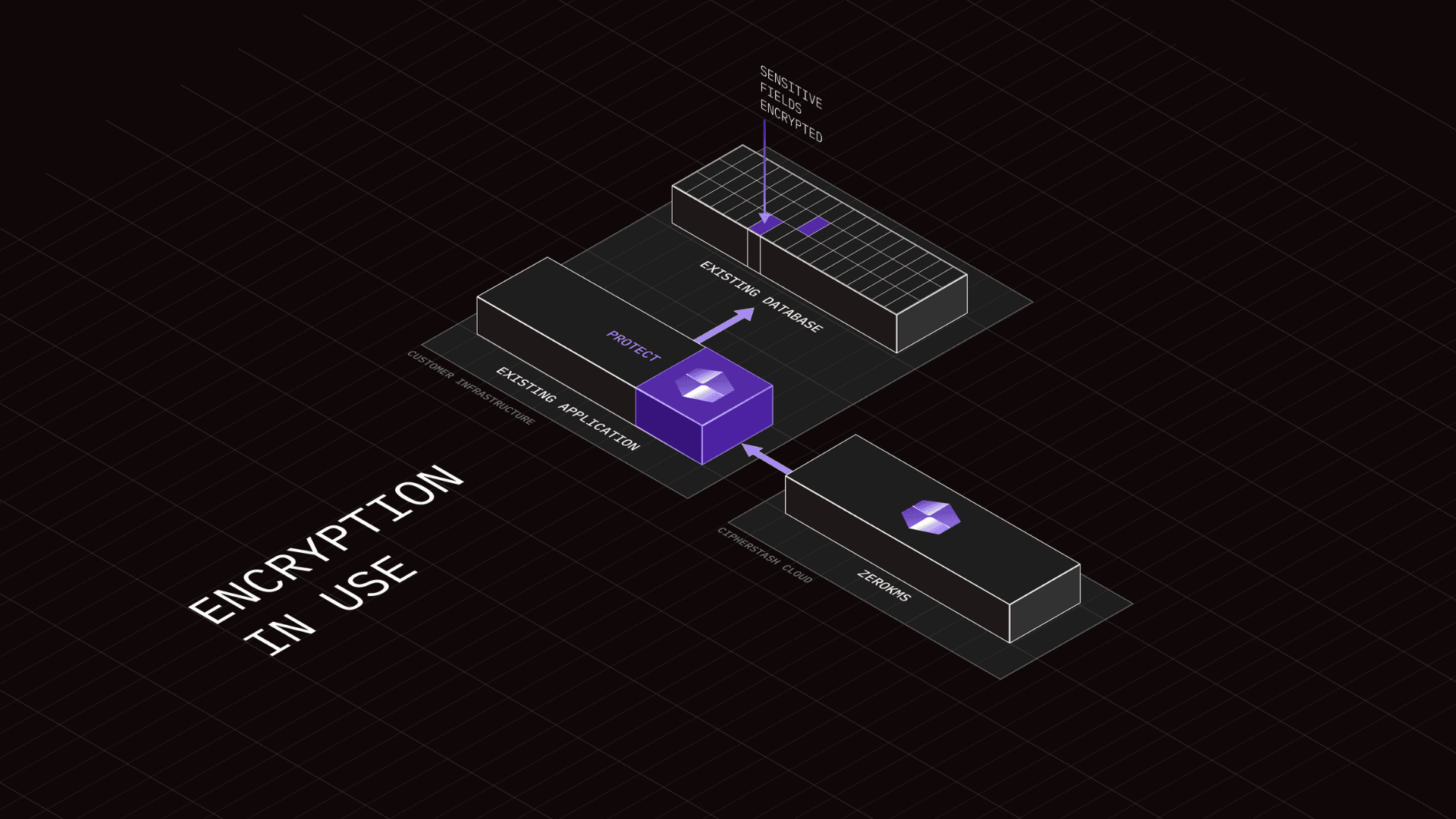
Encryption in use that protects individual values is a powerful way to keep data safe: it provides granular control, reduces the attack surface of any stored data and makes sure sensitive information is protected end-to-end.
However, if you’ve just started learning about how to use it, encryption can seem pretty daunting. Complex APIs, key management and “modes of operation” not only take time to understand, but are tricky to implement. Simple mistakes in implementation can lead to major security flaws even when everything appears to be working correctly.
In this post, we’ll compare three common options for encryption, with some look-outs and tips for ensuring a secure approach:
Local key management with the native
cryptopackageUsing AWS KMS through the AWS SDK for JavaScript
Using Protect.js from CipherStash
Considerations
Before jumping into the solutions, let’s touch on some of the things you should consider before choosing an encryption approach...
Encryption type
Encryption comes in 2 main forms: public-key or symmetric. Formally, these are referred to cryptographic schemes. We’ll just consider symmetric encryption in this article and specifically, AES (Advanced Encryption Standard).
AES is very fast (it can encrypt up to 4GB/s on a single core), is implemented in hardware by most CPU manufacturers and is very secure. Since being formally announced in 2001, no significant attacks have ever been found against AES.
Many libraries, including the Node.js crypto module, specify AES along with a key size and mode which are crucial to security.

Encryption Mode
The security of AES, is very dependent on its mode of operation (or just mode).
[!RECOMMENDATION] Use GCM mode (or GCM-SIV if available)
When encrypting data with AES, you must always be careful about which mode is used. Not only because decryption and encryption must use the exact same mode to function correctly, but because the choice of mode can dramatically affect the security of your system.
Mode | Name | Integrity | Performance |
CBC | Cipher Block Chaining | No | Poor |
CTR | Counter | No | Excellent |
CCM | Counter with CBC authentication | Yes | Good |
GCM | Galois Counter Mode | Yes | Excellent |
Some AES encryption modes provide message authentication which means decryption will fail if a message has been tampered with. In a new system, you should always choose one of these modes because non-authenticating modes like CBC have significant security weaknesses.
Key size
AES supports 3 different key-sizes: 128, 192 or 256 bits.
[!RECOMMENDATION] Use AES with 256-bit keys
In all 3 cases, the resulting encrypted value is the same size but larger keys provide stronger security by applying the underlying AES algorithm for more repetitions. Using a 256-bit key is only about 15% slower than a 128-bit key but the security improvement is significant. AES with 256-bit keys also provides resistance to attacks by a quantum computer.
Key management
Without effective key management, encryption is useless. It’s like installing a giant steel door on your house but leaving the key in the lock.
[!RECOMMENDATION] Use a cloud-based KMS like ZeroKMS
There are 3 main options for key management.
Local key - a single key stored with the application (e.g. with an env var)
Cloud KMS - services like AWS KMS or CipherStash ZeroKMS
Hardware Security Module (HSM) - specialised key storage for highly regulated environments
Security | Performance | Cost | Flexibility | |
Local key | Poor | Excellent | Free | Low |
Cloud KMS | Very good | Variable | Low-Medium | Medium-High |
HSM | Excellent | Medium | High | Low |
A local key is an encryption key that is stored with the application that’s using it such as in an environment variable. This seems like a simple approach until you consider some of the ways that things can go wrong. For example, if the key is compromised, an adversary could gain access to all the data the key had been used to encrypt. A new key would need to be generated and all data re-encrypted.
AES keys are also vulnerable to key wear-out which occurs when a single key is used to encrypt a large volume of data and can lead to complete recovery of the key by an attacker. In practice, key wear-out can occur after as little as 4GB of data has been encrypted!
[!CAUTION] A local key should be rotated once it has encrypted around 4GB of data or security can be significantly weakened
Cloud services like AWS KMS address many of the security shortcomings of using a local key. Most use offer a technique called envelope encryption which reduces the risk of key wear-out. However, this can introduce performance problems. Data key caching is often used to improve performance but this introduces new problems like how often to refresh keys and protecting the key-cache itself.
ZeroKMS extends the idea of envelope encryption to support bulk and streaming key operations which improves performance significantly (up to 14x that of AWS KMS) without the need for key caching.
Finally, HSMs, while extremely secure are typically used only for highly regulated environments such as banking or defence. This is primarily due to the high cost but also because they require a high-degree of expertise to operate. However, most cloud-based KMS (including AWS KMS and ZeroKMS) use HSMs internally.
With the considerations covered, let's look at some implementations.
Option 1: Node native crypto library
How it works
This is very much a build-it-yourself approach using the crypto module available in Node.js and a local key. It requires time and care, especially when it comes to managing keys and selection of the encryption settings (such as the mode).
Still, if you absolutely cannot rely on any 3rd party technologies then this is the path you’ll need to take. The Node Crypto API supports AES with 256-bit keys and the GCM mode. It also provides a high-degree of flexibility which makes it a good choice if you know what you're doing.
Pros
Complete control over your encryption strategy
Native open source tools for JavaScript/TypeScript developers
No external dependencies beyond your Node.js environment
Cons
Key exposure risk — managing keys locally can introduce human error or misconfiguration
No built-in lifecycle management — you must handle key rotation and expiry manually
DevOps overhead — you need robust processes for storing, distributing, and periodically rotating keys
Security risks — easy to use an insecure encryption configuration if you don't know what you're doing
Code Example
Below is a simple example of encrypting and decrypting a piece of text using the native crypto package (built into Node.js). This code uses symmetric encryption in AES-256-GCM mode.
1import { randomBytes, createCipheriv, createDecipheriv } from 'crypto';
2
3const ALGORITHM = 'aes-256-gcm';
4// In a real application, make sure to store and protect this key properly!
5const ENCRYPTION_KEY = randomBytes(32); // 256 bits for AES-256
6const AUTH_TAG_LENGTH = 12;
7
8function encrypt(text: string): string {
9 try {
10 // Generate a new IV for each encryption
11 const iv = randomBytes(16);
12 const cipher = createCipheriv(ALGORITHM, ENCRYPTION_KEY, iv, {
13 authTagLength: AUTH_TAG_LENGTH
14 });
15
16 // Encrypt the text
17 let encrypted = cipher.update(text, 'utf8', 'hex');
18 encrypted += cipher.final('hex');
19 const tag = cipher.getAuthTag();
20
21 // Prepend the IV to the encrypted text
22 return iv.toString('hex') + ':' + tag.toString('hex') + ':' + encrypted;
23 } catch (error) {
24 throw new Error(`Encryption failed: ${error}`);
25 }
26}
27
28function decrypt(encryptedText: string): string {
29 try {
30 // Split the IV and encrypted text
31 const [ivHex, tagHex, encryptedData] = encryptedText.split(':');
32 const iv = Buffer.from(ivHex, 'hex');
33 const tag = Buffer.from(tagHex, 'hex');
34
35 const decipher = createDecipheriv(ALGORITHM, ENCRYPTION_KEY, iv, { authTagLength: AUTH_TAG_LENGTH });
36 let decrypted = decipher.update(encryptedData, 'hex', 'utf8');
37 decipher.setAuthTag(tag);
38 decrypted += decipher.final('utf8');
39 return decrypted;
40 } catch (error) {
41 throw new Error(`Decryption failed: ${error}`);
42 }
43}
44
45// Example usage
46const secretMessage = "Sensitive Data";
47
48try {
49 // Encrypt
50 const encrypted = encrypt(secretMessage);
51 console.log("Encrypted Text:", encrypted);
52
53 // Decrypt
54 const decrypted = decrypt(encrypted);
55 console.log("Decrypted Text:", decrypted);
56} catch (error) {
57 console.error("Error:", error);
58}Option 2: AWS KMS and SDK for Node
Instead of using a local key, which as discussed above can lead to some nasty security problems, you can use a cloud-based key management service, such as AWS KMS.
How it works
AWS KMS is a managed service that handles the creation, storage, and rotation of cryptographic keys. You can use the AWS SDK for JavaScript to send requests to KMS. KMS then returns encrypted or decrypted data. Alternatively, the Amazon Encryption SDK offers a more flexible envelope encryption scheme but is more complex to use and is best suited to developers with cryptography expertise.
Pros
Fully managed keys — AWS handles generation, secure storage, rotation
AWS integration — works well with other AWS services like S3, DynamoDB, etc.
Multiple language support - supports C, Python and Java as well as JavaScript and Typescript
Cons
Deep AWS integration coupled with AWS services
Performance overhead—encrypting or decrypting data requires API calls to KMS for every key, which adds network latency
Cost — KMS charges per request, which can become expensive with high-volume workloads
Setup complexity — requires AWS credentials, IAM policies, and a general familiarity with AWS
Code Example
1import {
2 KMSClient,
3 EncryptCommand,
4 DecryptCommand,
5} from "@aws-sdk/client-kms";
6
7const kmsClient = new KMSClient({ region: "us-east-1" });
8// Replace with the ARN of your AWS KMS key
9const KeyId = "arn:aws:kms:us-east-1:123456789012:key/EXAMPLE-KEY-ID";
10
11async function encryptData(plaintext: string) {
12 const command = new EncryptCommand({
13 KeyId,
14 Plaintext: Buffer.from(plaintext, "utf-8"),
15 });
16 const response = await kmsClient.send(command);
17 return response.CiphertextBlob?.toString("base64");
18}
19
20async function decryptData(ciphertext: string) {
21 const command = new DecryptCommand({
22 CiphertextBlob: Buffer.from(ciphertext, "base64"),
23 });
24 const response = await kmsClient.send(command);
25 return response.Plaintext?.toString("utf-8");
26}
27
28async function run() {
29 const secretMessage = "Sensitive Data";
30
31 // Encrypt
32 const encrypted = await encryptData(secretMessage);
33 console.log("Encrypted (base64):", encrypted);
34
35 // Decrypt
36 if (encrypted) {
37 const decrypted = await decryptData(encrypted);
38 console.log("Decrypted:", decrypted);
39 }
40}
41
42run().catch(console.error);Option 3: Protect.js from CipherStash
Protect.js delivers the best of both worlds: enjoy the convenience of a fully managed service without the complexity and performance overhead of KMS, or the risks of local key management. Protect.js uses ZeroKMS, an efficient key management solution that sidesteps the overhead typical of cloud-based KMS options.
How it works
Pros
Simple implementation - simple interface makes implementation straightforward
Only secure settings - only uses secure encryption settings like mode and key size
High performance - up to 14x faster than AWS KMS
Cost effective - batched operations containing many keys are the same price as single keys
Cons
Only Typescript/JavaScript - Protect.js only supports JavaScript or TypeScript for now
Code example
Below is a quick example illustrating how straightforward Protect.js can be:
1import { protect, csTable, csColumn } from '@cipherstash/protect'
2
3const users = csTable('users', {
4 sensitive: csColumn.string(),
5});
6
7// Instantiate the Protect client (this sets up ZeroKMS under the hood)
8const protectClient = await protect(users);
9
10async function run() {
11 const secretMessage = 'Sensitive Data';
12
13 // Encrypt
14 const encrypted = await protectClient.encrypt(secretMessage, {
15 table: users,
16 column: users.sensitive,
17 });
18
19 if (encrypted.failure) {
20 throw new Error(encrypted.failure);
21 }
22
23 // Decrypt
24 const decrypted = await protectClient.decrypt(encrypted.data);
25 if (decrypted.failure) {
26 throw new Error(decrypted.failure);
27 }
28
29 console.log('Decrypted:', decrypted.data);
30}
31
32run().catch(console.error);Conclusion
When it comes to encrypting data in your JavaScript or TypeScript application, you have a few solid choices:
Local crypto library: Offers total control but requires you to handle key security, rotation, distribution, and the security risks of local key management.
AWS KMS: Manages many security concerns for you but can become expensive, introduces latency overhead, and complex implementation.
Protect.js: Blends the best elements of both, combining simple setup with high performance and bulletproof key management via ZeroKMS.
If you need an encryption solution that spares you the headache of manual key management, Protect.js stands out as the optimal choice. It’s quick to set up, protects you from common security pitfalls, and scales reliably—without the complexity or high cost of managed cloud services.
For more details, check out the Protect.js GitHub repository or CipherStash website. In under ten minutes, you can integrate enterprise-grade encryption into your application!